- Browse
- Post Exploitation Techniques
Results for "post-exploitation techniques"
 Status: Free TrialFree Trial
Status: Free TrialFree TrialSkills you'll gain: Disaster Recovery, Relational Databases, Database Architecture and Administration, Oracle Databases, Data Storage Technologies, Data Migration, Key Management, Data Integrity, Encryption, Data Loss Prevention, Data Security
Advanced · Course · 1 - 3 Months
 Status: PreviewPreviewC
Status: PreviewPreviewCCoursera
Skills you'll gain: AI Enablement, Amazon Web Services, AI Workflows, Integrated Development Environments, Software Development Tools, Software Development, Development Environment, Maintainability, Automation, Debugging
Intermediate · Course · 1 - 4 Weeks
 Status: Free TrialFree Trial
Status: Free TrialFree TrialSkills you'll gain: Autodesk Maya, Autodesk, 3D Modeling, Computer Graphics, Visualization (Computer Graphics), Image Quality
4.7·Rating, 4.7 out of 5 stars10 reviewsIntermediate · Course · 1 - 4 Weeks
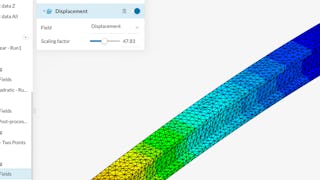
Skills you'll gain: Finite Element Methods, Simulation and Simulation Software, Data Validation, Simulations, Engineering Analysis, Verification And Validation, Engineering Design Process, Cloud Engineering, Mechanical Engineering, Scientific Visualization, Physics
Beginner · Guided Project · Less Than 2 Hours
 Status: NewNewStatus: Free TrialFree Trial
Status: NewNewStatus: Free TrialFree TrialSkills you'll gain: Server Side, Web Development, Web Scraping, Web Applications, Back-End Web Development, Integration Testing, Python Programming, Web Services, Extensible Markup Language (XML), Package and Software Management, Development Testing, Unit Testing, Performance Tuning, Cross Platform Development, Hypertext Markup Language (HTML), Debugging
4.9·Rating, 4.9 out of 5 stars20 reviewsMixed · Course · 1 - 4 Weeks
 Status: NewNewStatus: PreviewPreviewN
Status: NewNewStatus: PreviewPreviewNNortheastern University
Skills you'll gain: Text Mining, Data Mining, Time Series Analysis and Forecasting, Classification Algorithms, Big Data, Artificial Neural Networks, Regression Analysis, Data Science, Machine Learning Algorithms, Supervised Learning, Feature Engineering, Unsupervised Learning, Analytics, Predictive Modeling, Forecasting, Advanced Analytics, Deep Learning, Data Preprocessing
Intermediate · Course · 1 - 3 Months
Skills you'll gain: Model Deployment, Amazon Web Services, Cloud Deployment, Computer Vision, Cloud Computing, Application Deployment, Machine Learning
Beginner · Guided Project · Less Than 2 Hours
 Status: Free TrialFree TrialB
Status: Free TrialFree TrialBBoard Infinity
Skills you'll gain: Backlogs, Agile Product Development, Product Roadmaps, Stakeholder Communications, Release Management, Stakeholder Engagement, User Story, Stakeholder Management, Agile Methodology, Innovation, CI/CD, Product Lifecycle Management, Product Development, Prioritization, Scope Management, Maintainability
Intermediate · Course · 1 - 4 Weeks

Skills you'll gain: Object Oriented Programming (OOP), C++ (Programming Language), Development Environment, Computer Programming, Maintainability, Data Structures, Command-Line Interface, Debugging
Beginner · Course · 1 - 3 Months
 Status: Free TrialFree TrialL
Status: Free TrialFree TrialLL&T EduTech
Skills you'll gain: Mechanical Engineering, Construction, Construction Engineering, Civil Engineering, Hydraulics, Mechanical Design, Structural Engineering, Safety Standards, Hydrology, Environmental Engineering, Electrical Equipment, Construction Management, Energy and Utilities, Water Resource Management
Advanced · Course · 1 - 4 Weeks
 Status: NewNewStatus: PreviewPreview
Status: NewNewStatus: PreviewPreviewSkills you'll gain: Equities, Capital Markets, Investment Banking, Business Valuation, Financial Modeling, Global Marketing, Market Share, Financial Forecasting, Financial Analysis, Market Dynamics, Financial Statements, International Finance, Financial Regulations, Underwriting, Fundraising
Mixed · Course · 1 - 3 Months
 Status: Free TrialFree TrialB
Status: Free TrialFree TrialBBoard Infinity
Skills you'll gain: Apple iOS, Swift Programming, Apple Xcode, Mobile Development, User Interface (UI), User Interface (UI) Design, Debugging, Data Persistence, Data Management, Programming Principles, Application Programming Interface (API), Data Storage, Authentications
Beginner · Course · 1 - 4 Weeks
In summary, here are 10 of our most popular post-exploitation techniques courses
- Advanced Backup Management and Recovery Scenarios: Packt
- Code Generation with Amazon Q: Coursera
- MAYA Architecture - Lighting and Rendering with Mental Ray: EDUCBA
- Eine Einführung in die Finite Elemente Methode mit SimScale: Coursera
- Integrating Python for Web Systems, Testing, and Packaging: EDUCBA
- Machine Learning and Data Analytics Part 2: Northeastern University
- Implementando modelo Computer Vision en Amazon Sagemaker: Coursera
- Backlog Mastery, Product Ownership, and Industry Tools: Board Infinity
- Practical C++: Learn C++ Basics Step by Step: Packt
- Components of Hydropower Structures: L&T EduTech










